Establishing Site-to-Site VPN Connection
This section provides an overview, highlights pre-requisites, and walks through detailed step-by-step instructions to help you establish a site-to-site VPN connection between your on-premises network and the VPCs in your AWS environment.
1. Review the Solution
Review Note: Provide a diagram that is the overview of the solution.
2. Ensure Pre-requisites Are Satisfied
Non-overlapping IP Addresses
If you didn’t use a non-overlapping range from the start, you will need to either replace your initial set of development VPCs with VPCs that use non-overlapping IP addresses or implement Network Address Translation (NAT).
Static Public IP Address for Your Customer Gateway
In your on-premises environment, you will need to identify a static public IP address that will be associated with your Customer Gateway that will act as the on-premises side of the VPN site-to-site connection. You’ll use this IP address in the subsequent steps when you register your Customer Gateway in your AWS environment.
3. Register Your Customer Gateway in AWS
You will begin by making changes in the network-prod account you set up earlier.
- As a Cloud Administrator, use your personal user to log into AWS SSO.
- Select the
network-prodAWS account - Select
Management consoleassociated with theAWSAdministratorAccessrole. - Select the appropriate AWS region.
- Navigate to
VPCand click onCustomer Gatewaysin the left navigation - Click the button
Create Customer Gateway - Fill out the Customer Gateway form details. Some suggested fields are below:
| Field | Recommendation |
|---|---|
Name |
example-network-on-prem-01 |
Routing |
Dynamic Routing |
BGP ASN |
6500 |
IP Address |
Enter the value of the public IP Address of your on-premises gateway address for your VPN |
Certificate ARN |
Leave empty |
Device |
Leave empty |
Customer Gateway ID: Note the Customer Gateway ID for the newly created Customer Gateway. You will use this in later steps.
4. Create a Transit Gateway in your Network account
- While you are still in the
VPN Consoleadministration, click onTransit Gatewaysin the left navigation - Click the button
Create Transit Gateway - Fill out the Transit Gateway form details. Some suggested fields are below:
| Field | Recommendation |
|---|---|
Name tag |
acme-network-tgw-01 |
Description |
Transit Gateway in order to route traffic to/from On-Prem network as well as within VPCs |
Transit Gateway ID: Please note down the Transit Gateway ID for the recently created Transit Gateway. You will use this in later steps.
5. Create a VPN Transit Gateway Attachment in your Network account
- While you are still in the
VPN Consoleadministration, click onTransit Gateway Attachmentsin the left navigation - Click the button
Create Transit Gateway Attachment - Fill out the Transit Gateway Attachment form details. Some suggested fields are below:
| Field | Recommendation |
|---|---|
Transit Gateway ID |
Select value from dropdown that matched the ID of the Transit Gateway you just created. |
Attachment Type |
VPN |
Customer Gateway |
Existing |
Customer Gateway ID |
Select value from dropdown that matched the ID of the Customer Gateway you just created. |
Routing options |
Dynamic (requires BGP) |
Transit Gateway Attachment Name: Once created, it is recommended to provide a name to the Transit Gateway Attachment. To do this, select the checkbox of the row for the attachment you just created. Click the pencil icon under the Name column. Enter a name (i.e. acme-routing-tgw-vpn-01).
VPN: As a result of the VPN attachment being provisioned, you will notice that a Site-to-Site VPN Connection resource has been created for the attachment.
6. Configure your Site-to-Site VPN connection
- While you are still in the
VPN Consoleadministration, click onSite-to-Site VPN Connectionsin the left navigation - Select the VPN just created in the list of VPN connections
- Click on the
Actionsbutton and selectModify VPN Connection - Edit the name for your VPN connection. (Suggestion: acme-routing-vpn-onprem-01)
- Download the VPN configuration information by clicking
Download Configuration - Use the configuration to configure you on-premises VPN gateway.
VPN Configuration: Select your Vendor, Platform, and Software from the dropdowns. If you specific vendor is not available, select Generic. As a best practice, AWS provides your configuration file with a primary and secondary VPN configuration. This allows for redundancy of your VPN connection.
Once your VPN is configured on-premises, navigate back to the Site-to-Site VPN Connections within the VPC console. Select the row of your VPN connection. At the botton of the page, select the Tunnel Details tab. Verify that the Status has changed from “DOWN” to “UP” (this may take a few minutes).
Troubleshooting tips:
- Ensure that routing tables on AWS and router configurations (on-premises) are setup to allow communication.
- Ensure VPC route tables associated with subnets route traffic destined for the other site to the local VPN gateway instance.
- If using Transit Gateway on the remote site, ensure that VPC route tables are configured to route traffic destined for the other site to the Transit Gateway. (Although the built-in BGP support in this stack will ensure that both the local VPN gateway’s route information and the remote Transit Gateway’s route table will be automatically configuired, you still need to ensure that the VPC route tables in both sites are properly configured).
7. Create a Transit Gateway Attachment to connect to your VPC
- While you are still in the
VPN Consoleadministration, click onTransit Gateway Attachmentsin the left navigation - Click the button
Create Transit Gateway Attachment - Fill out the Transit Gateway Attachment form details. Some suggested fields are below:
| Field | Recommendation |
|---|---|
Transit Gateway ID |
Select value from dropdown that matched the ID of the Transit Gateway you just created. |
Attachment Type |
VPC |
DNS support |
enable (checked) |
VPC ID |
Select the value form the dropdown for that matches thee ID of the dev VPC in your account. |
Subnet IDs |
Select a subnet from each availability zone - preferrably a private subnet |
8. Edit your VPC Route Table to add a route for your On-Premises CIDR
- While you are still in the
VPN Consoleadministration, click onRoute Tablesunder Virtual Private Cloud in the left navigation - Select your route table in the list
- Select the
Routestab at the bottom of the page and clickEdit routes - Add a new route with the values below:
| Field | Recommendation |
|---|---|
Destination |
Fill in with your on-premises CIDR range (i.e. 172.31.0.0/16 |
Target |
Select value from dropdown that matched the ID of the Transit Gateway you just created. |
On-premises VPN Routes: You will need to make similar types of changes to the routing rules with your on-premises infrastructure in order to route to the reserved CIDR ranges you have allocated for your AWS environment(s).
9. Enable resource sharing in your master account
You will need to enable sharing resources within your AWS Organizations from your master account. THis will allow you to access Transit Gateway from each of your accounts created and maintained within Control Tower.
- As a Cloud Administrator, use your personal user to log into AWS SSO.
- Select the
masterAWS account - Select
Management consoleassociated with theAWSAdministratorAccessrole. - Select the appropriate AWS region.
- Navigate to
Resource Access Manager - Click the
Settingsin the left navigation panel - Check the
Enable sharing within your AWS Organizationscheckbox, then click theSave settingsbutton
Find your Organization ID: Navigate to AWS Organizations and click on any of the accounts to open the information panel on the right. Within the ARN, after the word account, you will see your Organization ID (starts with o-). Note this down for the next set of steps.
10. Sharing your Transit Gateway to your other accounts
You will use AWS Resource Access Manager (RAM) to share your Transit Gateway for VPC attachments across your accounts and/or your organizations in AWS Organizations.
- As a Cloud Administrator, use your personal user to log into AWS SSO.
- Select the
NetworkAWS account - Select
Management consoleassociated with theAWSAdministratorAccessrole. - Select the appropriate AWS region.
- Navigate to
Resource Access Manager - Click the
Create a resource sharebutton - Fill out the resource share form details. Some suggested fields are below:
| Field | Recommendation |
|---|---|
Name |
acme-network-tgw-share-01 |
Select resource type |
Transit Gateways (and select your Transit Gateway) |
Allow external accounts |
(checked) |
Add AWS account number, OU or organization |
Enter the Organization ID from your master account (captured in the above steps) |
11. Configure Transit Gateway with another one of your accounts in your organization
VPC: If you do not already have a VPC in your account, please create one.
- As a Cloud Administrator, use your personal user to log into AWS SSO.
- Select the desired AWS account to log into
- Select
Management consoleassociated with theAWSAdministratorAccessrole. - Select the appropriate AWS region.
- Navigate to
VPCand click onTransit Gateway Attachmentsin the left navigation - Click the button
Create Transit Gateway Attachment - Fill out the Transit Gateway Attachment form details. Some suggested fields are below:
| Field | Recommendation |
|---|---|
Transit Gateway ID |
Select value from dropdown that matched the ID of the Transit Gateway you just created. |
Attachment Type |
VPC |
DNS support |
enable (checked) |
VPC ID |
Select the value form the dropdown for that matches thee ID of the dev VPC in your account. |
Subnet IDs |
Select a subnet from each availability zone - preferrably a private subnet |
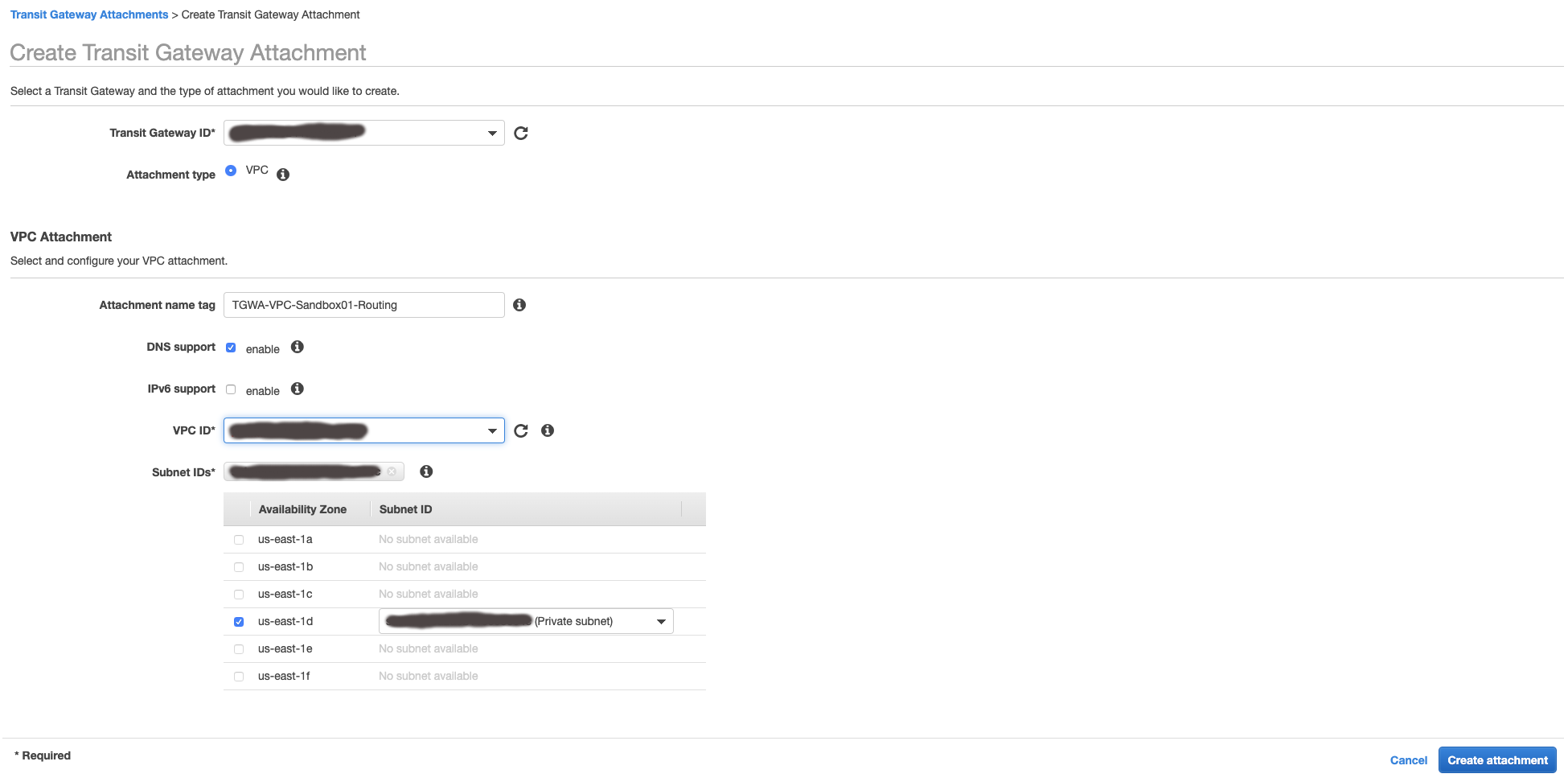
Transit Gateway Attachment - Pending Acceptance: If your account is not setup as Auto accept shared attachments: enable, after you create the Transit Gateway Attachment, the status will show as pending acceptance. You will need to log into your Network account and accept the Transit Gateway Attachment by selecting it in the VPC console and going to Actions|Accept. Once this is done, the VPC will show up under the Transit Gateway Route Table - Associations.
Transit Gateway Route Tables - Propagations: If your Transit Gateway is configured for Default propagation route table: enable. If not, you will need to log into your Network account, navigate to the Transit Gateway Route Tables, select your route table, go to the Propagations tab, and create a new propagation to the VPC in your attachment account.
12. Configure the Route Tables in the account you just setup a Transit Gateway Association
- As a Cloud Administrator, use your personal user to log into AWS SSO.
- Select the desired AWS account to log into
- Select
Management consoleassociated with theAWSAdministratorAccessrole. - Select the appropriate AWS region.
- Navigate to
VPCand click onRoute Tablesin the left navigation - Select your route table in the list
- Select the
Routestab at the bottom of the page and clickEdit routes - Add a new route with the values below:
| Field | Recommendation |
|---|---|
Destination |
Fill in with your on-premises CIDR range (i.e. 172.31.0.0/16 |
Target |
Select value from dropdown that matched the ID of the Transit Gateway you just created. |
Repeat for additional accounts: You will repeat steps 9 and 10 for each of the accounts within your organization that you want to be able to communicate with your on-premises network.